2022 Reports 5 to 8 of the Auditor General of Canada to the Parliament of Canada
Report 7—Cybersecurity of Personal Information in the Cloud
At a Glance
Information stored digitally, whether on-premises in data centres or in the cloud, is exposed to risks of being compromised. Overall, we found that the requirements the government had in place to reduce the security risks of storing information in the cloud were not always followed by the departments we audited. In addition, these requirements and their corresponding roles and responsibilities were not always clear, resulting in inconsistent implementation and increased risks. This is important because the Treasury Board of Canada Secretariat has directed departments to consider moving applications and databases to the cloud, so increasing amounts of Canadians’ personal information are moving there. At the same time, cyberattacks are becoming more frequent and sophisticated. The risk of significant impacts on the government and its operations is growing.
The government must take immediate action to strengthen how it prevents, detects, and responds to cyberattacks. It should do this now, while departments are still in the early stages of moving personal information to the cloud. This action includes strengthening key security controls to prevent, detect, and respond to security breaches. It also includes clarifying shared roles and responsibilities for cybersecurity—which are highly complex in a cloud environment—so that all departments know exactly what they should be doing.
We also found that, 4 years after the Treasury Board of Canada Secretariat first directed departments to consider moving to the cloud, it had still not provided a long-term funding approach for cloud adoption. It had also not given departments tools to calculate the costs of moving to or of operating in the cloud and securing the information stored in it. Departments need both a funding approach and costing tools to ensure that the people, expertise, skills, training, funding, and other resources they need to secure cloud-based information are available to prevent and address the greatest threats and risks. A funding approach and costing tools are essential for cloud adoption and would strengthen Canada’s cyber-defence capabilities both at the departmental level and government-wide.
Why we did this audit
- Information stored digitally, whether on‑premises in data centres or in the cloud, is exposed to risks of being compromised.
- Federal departments are increasingly moving software applications and databases into the cloud, including some that handle or store Canadians’ personal information. Departments must work together to protect this information from a number of risks, including cyberattacks.
- Cybersecurity breaches are on the rise, and strong controls to prevent, detect, and respond to them can reduce the risk of breaches.
Our findings
- There were weaknesses in departments’ controls for preventing, detecting, and responding to cyberattacks.
- The roles and responsibilities for ensuring cloud cybersecurity were unclear and incomplete.
- The Treasury Board of Canada Secretariat did not provide departments with a costing model or funding approach for cloud services.
- Public Services and Procurement Canada and Shared Services Canada did not include environmental criteria in their procurement of cloud services.
Key facts and figures
- Departmental spending on cloud services government-wide has increased significantly year over year, from $35 million in 2018 to almost $120 million in 2021.
- Digital technologies are expected to be responsible for 8% of global greenhouse gas emissions by 2025 and for up to 14% by 2040.
The 3 departments we selected for this audit were using a variety of short-term funding measures to support their cloud and cybersecurity operations, including reallocating funds that had been intended for other purposes.
Highlights of our recommendations
- In consultation with Shared Services Canada and Public Services and Procurement Canada, the Treasury Board of Canada Secretariat should clarify who is responsible for the initial validation and ongoing monitoring of cloud guardrail controls.
- The Treasury Board of Canada Secretariat should ensure that the Government of Canada Cyber Security Event Management Plan applies to the evolving cloud environment and shared responsibilities, review and test it at least annually, and update it as needed.
- In consultation with Shared Services Canada and other departments, the Treasury Board of Canada Secretariat should develop and provide a costing model to help departments make informed decisions about moving to the cloud and Help departments determine their long-term operational funding needs.
Please see the full report to read our complete findings, analysis, recommendations and the audited organizations’ responses.


Goal 12 aims to ensure sustainable consumption and production patterns. One of its targets is to “promote public procurement practices that are sustainable, in accordance with national policies and priorities.”
In 2017, Canada established the Greening Government Strategy with the expectation that all federal government organizations would incorporate environmental considerations into their procurement processes. The strategy recommended that departments encourage suppliers to disclose their greenhouse gas emissions and environmental performance information.
In 2020, the Greening Government Strategy was presented as a Government of Canada directive. It indicates that Canada intends to achieve net‑zero emissions by 2050 in its operations, including the procurement of goods and services. It also indicates that the government would include criteria aimed at reducing greenhouse gas emissions in its procurements for goods and services with a high environmental impact. As noted in the May 2022 Report of the Commissioner of the Environment and Sustainable Development on the Greening Government Strategy, progress to date suggests that the government is falling short on meeting its emission-reduction goal.
At the time of the audit, the Government of Canada was updating its cloud adoption strategy. The most recent draft, dated February 2022, included 10 items intended to help departments achieve business value. One item involved contributing to the government’s overall sustainable development objectives by “providing highly-efficient enterprise-scale infrastructure that reduces [greenhouse] gas emissions and promotes the greening of government.”
Visit our Sustainable Development page to learn more about sustainable development and the Office of the Auditor General of CanadaOAG.
Exhibit highlights
The Government of Canada established 12 cloud guardrails that serve as a minimum set of security controls
| Cloud guardrails | Objective |
|---|---|
|
1. Protect root/global administrator account |
Protect the root or master account that was used to establish the cloud service. |
|
2. Management of administrative privileges |
Establish access control policies and procedures to manage administrative privileges. |
|
3. Cloud console access |
Limit access to authorized users and Government of Canada devices. |
|
4. Enterprise monitoring accounts |
Create role-based accounts to enable enterprise monitoring and visibility. |
|
5. Data location |
Establish policies to restrict sensitive Government of Canada applications and information to approved geographic locations. |
|
6. Protection of data at rest |
Protect data at rest by default (for example, storage) for cloud-based applications. |
|
7. Protection of data in transit |
Protect data transit networks by using appropriate encryption and network safeguards. |
|
8. Segment and separate |
Segment and separate information according to its sensitivity. |
|
9. Network security services |
Establish external and internal network perimeters, and monitor network traffic. |
|
10. Cyber-defence services |
Establish a memorandum of understanding for defensive services and threat-monitoring protection services. |
|
11. Logging and monitoring |
Enable logging of network and system information and events for the cloud environment and for cloud-based workloads. |
|
12. Configuration of cloud marketplaces |
Restrict the use of commercial software from third-party cloud service providers to products approved by the Government of Canada. |
|
Source: Adapted from Government of Canada Cloud Guardrails, Government of Canada |
|
Cloud adoption comes with short- and long-term cybersecurity costs for departments
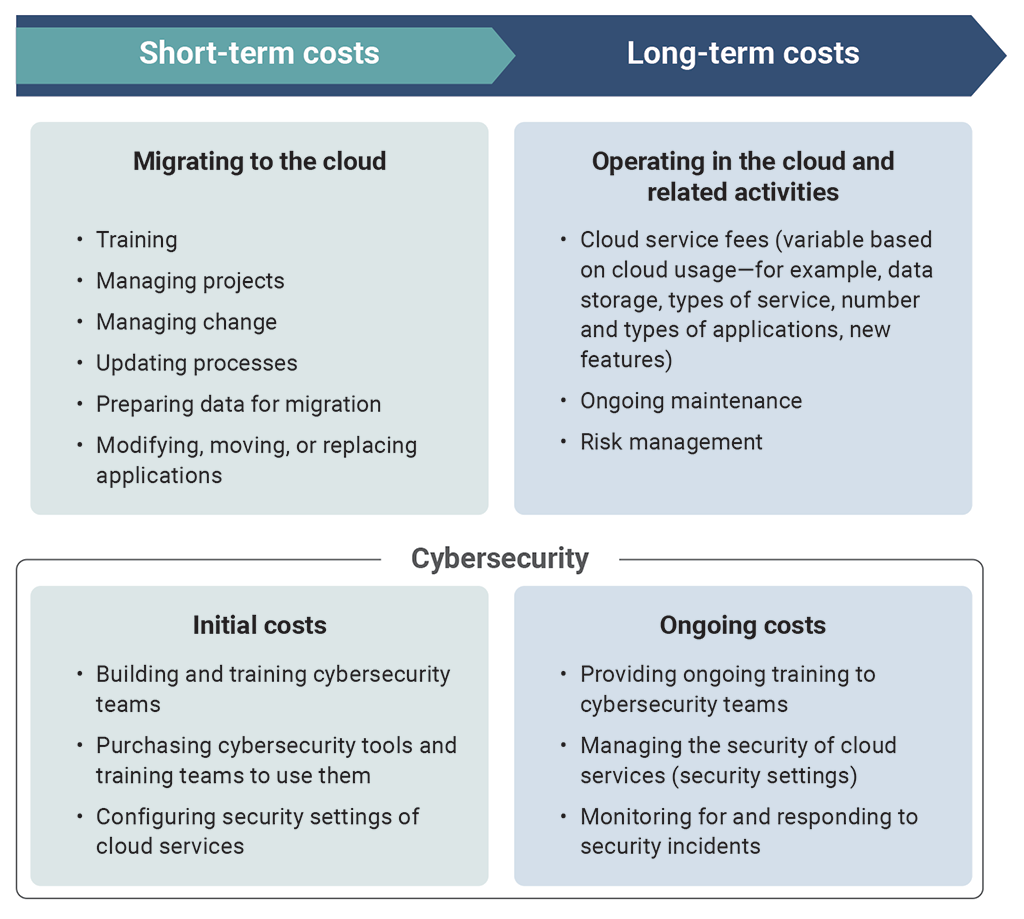
Note: These lists are meant to illustrate some of the cost considerations involved. They are not comprehensive.
Text version
This chart shows some of the short- and long-term costs of cloud adoption for departments (federal organizations).
In the short term, migrating information to the cloud involves costs for the following tasks:
- training
- managing projects
- managing change
- updating processes
- preparing data for migration
- modifying, moving, or replacing applications
Federal organizations also have initial and short-term costs related to the following tasks for cybersecurity:
- building and training cybersecurity teams
- purchasing cybersecurity tools and training teams to use them
- configuring security settings of cloud services
Over the long term, operating in the cloud and performing related activities involve costs for the following:
- cloud service fees (variable based on cloud usage—for example, data storage, types of service, number and types of applications, new features)
- ongoing maintenance
- risk management
Federal organizations also have long-term and ongoing costs related to the following tasks for cybersecurity:
- providing ongoing training to cybersecurity teams
- managing the security of cloud services (security settings)
- monitoring for and responding to security incidents
Infographic

Text version
Cybersecurity of Personal Information in the Cloud
Although the federal government had requirements for securing information in the cloud, these requirements were not always clear, and the departments we looked at were not following all of them.
Cloud storage
Cloud storage is one of the ways government saves information online so that it can be easily accessed at any time from any location.
Data is created by users through different devices, such as computers, phones, and tablets. This data is stored in the Government of CanadaGC Cloud and later accessed by people who need it. The Government of Canada can use cloud servers on demand, paying only for what it needs.
Protecting personal information in the cloud
When federal organizations store information in the cloud, they are responsible for ensuring the security of that information.
Some ways that the government protects information:
- Inspect the physical facilities where protected information is stored.
- Plan how to detect and respond to security breaches.
- Identify security requirements and responsibilities in contracts with cloud service providers.
- Establish and follow security controls, known as guardrails, to protect data.
What is a guardrail and how does it work?
Federal organizations that use cloud services are supposed to implement and follow Government of Canada guardrails—a baseline set of controls—to protect the information that they store or transmit using the cloud.
Guardrail examples
The following guardrails protect data that is in transit:
- Encryption
- Network safeguards
The following guardrails provide network security:
- Establish network perimeters
- Monitor network traffic
Our audit found that guardrail controls were inconsistently applied and monitored. This increases the risk of cyberattacks and that Canadians’ personal information in the cloud could be compromised.
Cyberattacks could result in
- government service shutdowns
- failure or destruction of critical infrastructure (such as bank shutdowns and power failures)
- exposure of personal data and potential identity theft
Cyberattacks are becoming more frequent and sophisticated.
The government needs to take action now while federal organizations are in the early stages of moving information to the cloud, to strengthen how it prevents, detects, and responds to cyberattacks.
Related information
Entities
Tabling date
- 15 November 2022
Related audits
- 2021 Reports of the Auditor General of Canada to the Parliament of Canada
Report 1—Procuring Complex Information Technology Solutions
Parliamentary hearings
